RiscZero
Key Takeaways
- RISC Zero is developing a zero-knowledge virtual machine to enhance the security and reliability of distributed applications.
- The zkVM technology allows a program's output to contain proof of origin and accurate execution, eliminating the need for a trusted third party and enabling previously centralized applications to become decentralized.
- Developing zkApps on RISC Zero is almost as simple as building any other Rust project, without needing to learn a custom language or advanced math or cryptography.
- RISC Zero has several use cases, including Spire, zkFHE, and zkPoEX, among others.
1. Overview
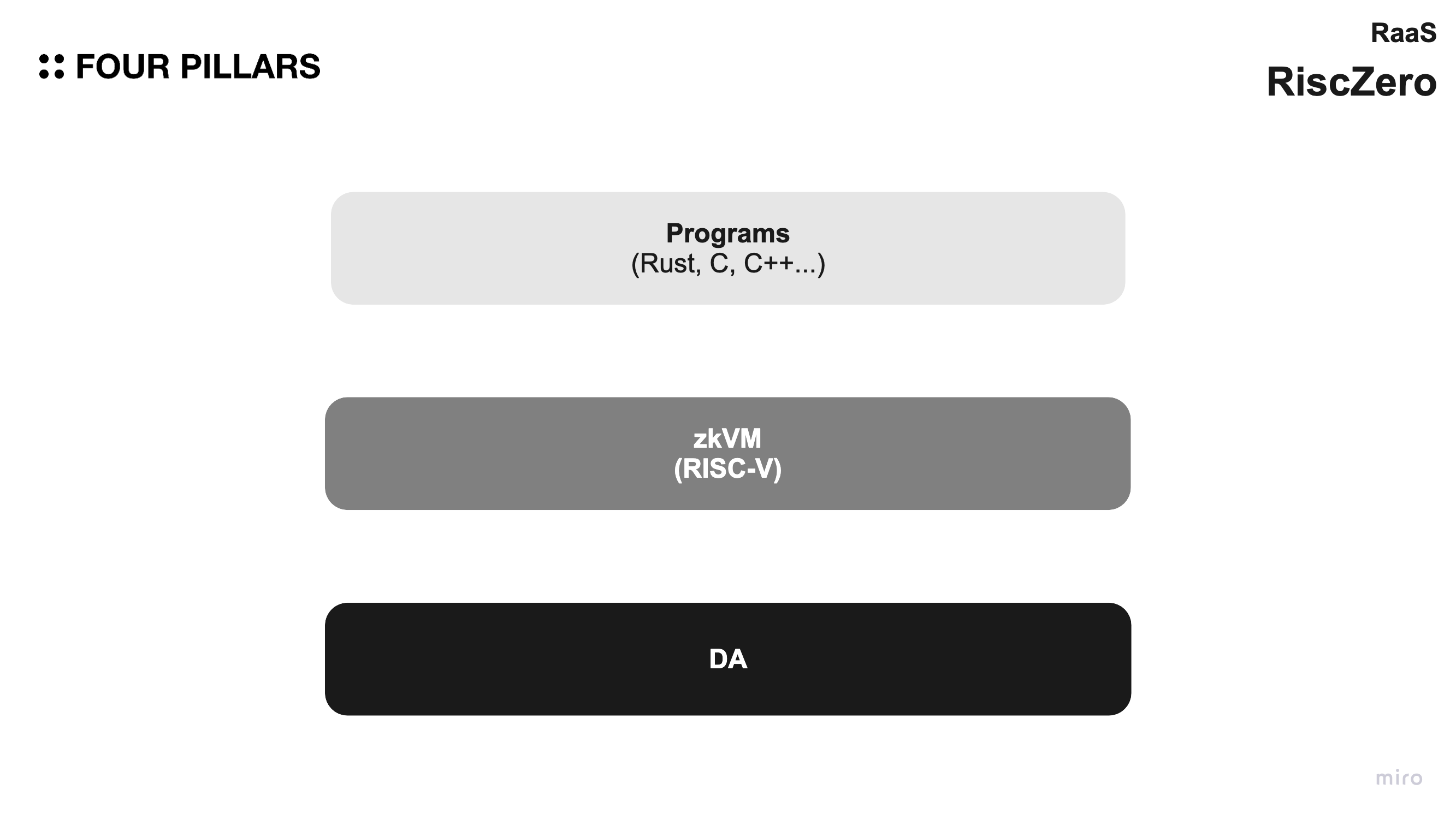
RISC Zero is working on the RISC Zero zero-knowledge virtual machine (zkVM) to improve the security and reliability of distributed applications. This implementation bridges the gap between zero-knowledge proof (ZKP) research and popular programming languages like C++ and Rust.
The zkVM technology enables a program's output to contain proof of origin and accurate execution, which a recipient can verify without access to the program's inputs. This verification capability eliminates the need for a trusted third party, allowing previously centralized applications to become decentralized. This shift has significant implications for the durability and economics of managing computing infrastructure.
2. Execution
The RISC Zero zero-knowledge virtual machine (zkVM) enables users to prove the accurate execution of arbitrary Rust code. By leveraging existing Rust packages, powerful and easily verifiable zero-knowledge applications can be created.
A zero-knowledge virtual machine (zkVM) is a virtual machine that runs trusted code and generates proofs that authenticate the zkVM output. RISC Zero's zkVM implementation is based on the RISC-V architecture, which runs code and generates a computational receipt.
Developing zkApps on RISC Zero is almost as simple as building any other Rust project. There is no need to learn a custom language or any advanced math or cryptography. Also, some other languages like C, C++, and python are also supported since they compile down to RISC.
2.1 Components
A zero-knowledge virtual machine (zkVM) application is composed of two main programs: the guest program and the host program. The guest program is the part of the application whose execution will be verified by the zkVM, while the host program is responsible for executing and proving the guest program's execution.
3. Settlement
To ensure that a zkVM application runs correctly, we take the following steps:
- Compile the guest program into an ELF binary.
- Run the ELF binary with the executor and record the execution trace.
- Validate and prove the execution trace using the prover, which will provide a receipt.
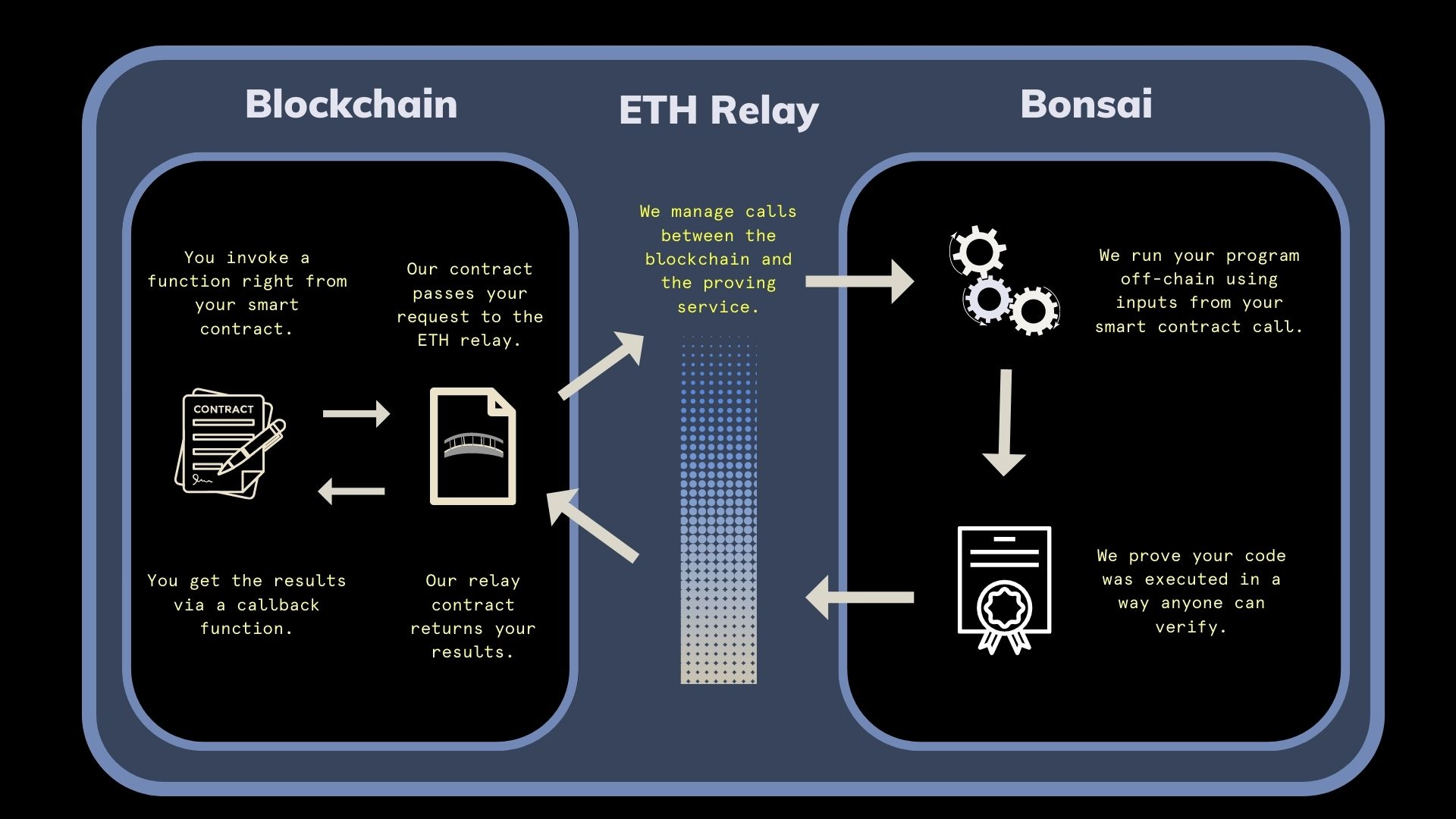
3.1 Bonsai
Bonsai is a zero-knowledge proof network that enables any chain, protocol, or application to leverage ZK proofs. It is highly parallel, programmable, and efficient. Bonsai's zero-knowledge proving network allows for direct integration of ZK proofs into smart contracts without requiring custom circuits. This allows ZK to be integrated into dApps on any EVM chain and potentially support any other ecosystem.
Bonsai's zkVM is the foundation of the network and allows for wide language compatibility, supporting provable Rust code and enabling zero-knowledge provable code in any language that compiles to RISC-V, such as C++, Solidity, Go, and more. By combining recursive proofs, a bespoke circuit compiler, state continuations, and continuous improvements to the proving algorithm, Bonsai enables anyone to generate highly performant ZK proofs for a variety of applications.
4. Data Availability
X
5. Interoperability
X
6. Use Cases
6.1 Spire
Introducing Spire - an L3 protocol — Spire
6.2 zkFHE
Verifiable and confidential computation based on ZKP and FHE
https://github.com/emilianobonassi/zkFHE
RISC Zero: "As we continue highlighting work that's emerging from the RISC Zero community, we're excited to put a spotlight on @emilianobonassi's work bringing homomorphic encryption (FHE) into the zkVM. https://t.co/riRxK3j9ci 1/7"
zkFHE allows for confidential computation that can be verified, using a combination of zero-knowledge proof (ZKP) and fully homomorphic encryption (FHE) technologies. FHE is a form of encryption that enables computations to be performed on encrypted data without decrypting it first, maintaining data confidentiality. zkFHE ensures the correctness of computation with ZKP, all powered by the risc0 zero-knowledge virtual machine (zkVM). A proof of concept (PoC) has been created to showcase the approach for private computation in a public environment without sacrificing data availability. This demonstration balances the need for privacy and the necessity for data availability in a secure public computational environment.
6.3 zkPoEX
https://github.com/zkoranges/zkPoEX
zkPoEX (zk proof of exploit) has been a Proof-of-Concept to facilitate communication and collaboration between security experts and teams in the DeFi space. The goal is to enable white hat hackers to report live vulnerabilities in smart contracts while maintaining the confidentiality of the exploit.
The problem with bug bounty programs in the DeFi space is that they can be difficult to run and maintain, may not always be honored, and may not offer sufficient compensation for white hats. This can lead to a lack of incentive for hackers to report vulnerabilities, which can ultimately result in a less secure DeFi ecosystem.
The solution offered by RISC Zero allows auditors to safely generate a zero-knowledge proof of exploit without revealing the actual exploit. With zero-knowledge proofs, the auditor can prove that they know of a transaction that can produce an undesirable change of state in certain contracts, without revealing the specifics of the exploit. Since the auditor is not giving away the exploit, the project is incentivized to work with the auditor to fix the vulnerability. This facilitates communication and collaboration between hackers and project owners for a more secure DeFi ecosystem.
6.4 LayerN
6.5 OP-Stack zk PoC
https://github.com/ethereum-optimism/ecosystem-contributions/issues/61#issuecomment-1611869982
6.6 …Hackathon
7. Team
- Brian Retford (CEO, Co-Founder)
- Frank Laub (CTO, Co-Founder)
- Jeremy Bruestle (CSO, Co-Founder)
8. Resources
- Website | Docs | Blog |Twitter
- by RiscZero
- https://www.risczero.com/docs/explainers by RiscZero
- Introduction | RISC Zero Developer Docs by RiscZero
